Digital banking is mobile lending service deposits payments marketplaces evolving accelerating design thinking open technology data your brand leasing
Everything has changed. It’s time to transform your technology, your customer relationships, and your entire business to fit a new set of expectations and opportunities.
Our Solutions
- For Commercial
- For Consumer
- For Fintech

What’s next in commercial banking
Introducing Q2 Catalyst: an extensive, holistic digital solution for commercial banking. Win more, onboard faster, serve better, and grow stronger relationships. With treasury management tools, small business solutions, relationship pricing, a fintech marketplace, and more, Q2 Catalyst is a growth engine for your business and your community.
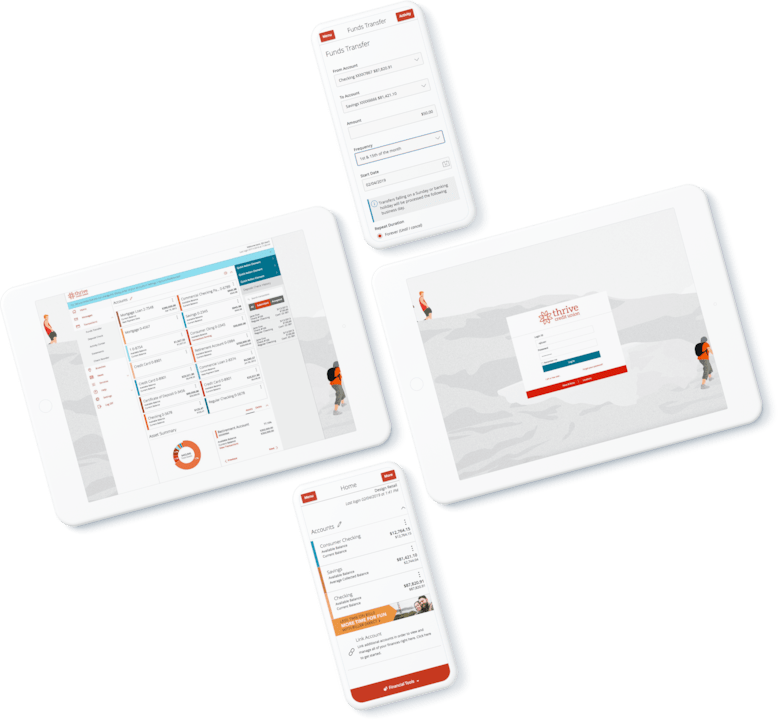
Consumers are looking for more than just checking accounts or debit cards.
They’re looking for quick, intuitive account opening, easy online borrowing, seamless security, and financial wellness tools and advice—including new ways to save, send money, and make purchases.

It’s your legacy that matters.
Legacy financial technology has blocked innovation for too long. The market is hungry for new solutions, pricing structures, and experiences.
A Proven Partner
The experience, innovation, and expertise you need to evolve, engage, and compete in an increasingly digital world.

>20M Users
The Q2 digital banking platform serves over 20 million end users.

>1.5B Saved
In 2021, Q2 prevented over 1.5 billion in business banking check fraud.

>1M Onboarded
We onboarded over a million new financial accounts last year.

>150% Growth
We’ve improved our customers’ digital marketing success rates by over 150%.
Introducing
Q2 Catalyst
Extensive digital solutions for commercial banking
Win More
Onboard Faster
Serve Better
Grow Relationships
The Latest and Greatest at Q2
Q2 Catalyst
Redefine what’s next in commercial banking with a comprehensive portfolio of digital solutions.
Innovation in Action
Leverage innovative offerings from our vast ecosystem to stay relevant, competitive, and on-the-grow.

It began with a mission
Q2 builds stronger, more diverse communities by strengthening the financial institutions that serve them.
Community banks and credit unions are the backbone of the financial world. Our mission is to keep it that way—even as those communities, their cultures, and their connections move deeper into the digital world.
The ways our customers win
Customer Stories
Browse All →-
Generations Federal Credit Union partners with Q2 to attract younger members
Membership of younger population grew and overall membership increased
-
Q2 helps Amplify Credit Union go fee-free
Grew checking accounts 5% faster and savings accounts 9% faster
-
FAIRWINDS Credit Union improves member experience with Q2
216% increase in ACH transactions
-
Tri Counties Bank increases online account openings with Q2
Online account openings increased by 75%


